URGENT UPDATE: 05/14/2017: MONDAY WILL BRING RENEWED ATTACKS.
FROM THE BBC: Europol's executive director Robert Wainwright says that there were at least 200,000 victims across 150 countries so far, and that number will go up on Monday morning when people go back to work.
Wainwright said: "We're in the face of an escalating threat, the numbers are going up.
Europol is the EU's law enforcement and intelligence agency. It's working with the FBI to track down the criminals responsible for the malware, but Wainwright said this was "very difficult."
"We have never seen anything like this," he said. "We've seen the rise of ransomware becoming the principal cyber threat, but this is something we've never seen before — the global reach is unprecedented."
The anonymous researcher who managed to slow the original attack on Friday also told the BBC there was "another one coming ... quite likely on Monday." DANGER TO PERSONAL COMPUTERS
“Many of these were from attachments to spam emails that appeared to contain invoices, job offers, security warnings and other files that looked legitimate, like PDF files,” said Matt Loria with Auxiom, a business IT firm in Madison Heights. “The crazy thing is that everyone is vulnerable,” Loria said.
ABOVE:
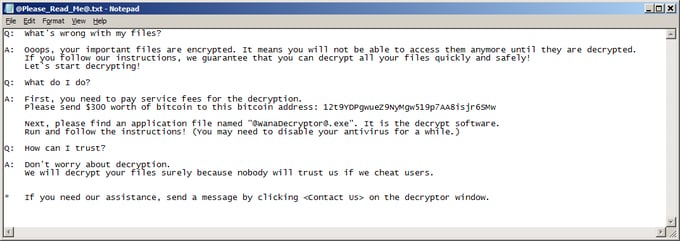
Screenshots of apparent ransomware attack messages sent to NHS England trusts https://t.co/jODkWomGPA pic.twitter.com/uc2HlGH9yM— BBC Breaking News (@BBCBreaking) May 12, 2017
"We saw the first version of WanaCrypt0r in February and now the ransomware is available in 28 different languages, from languages like Bulgarian to Vietnamese. Today at 8 am CET, we noticed an increase in activity of this strain, which quickly escalated into a massive spreading, beginning at 10 am.
MAY 12, 2017
THE WORLD RUNS ON COMPUTERS TODAY, SO THE NEW FORM OF WARFARE IS CYBER-ATTACKS,
WE MAY BE SEEING "CYBER WORLD WAR I", SOME NEWS SITES SAID.
NATIONS, INDUSTRY, THE MILITARY AND INDIVIDUALS ARE ALL 'UNDER SIEGE' AND THE TECHNOLOGY USED TO HACK INTO COMPUTER SYSTEMS IS GROWING BY LEAPS AND BOUNDS.
SUCH ATTACKS THREATEN THE ECONOMIES OF NATIONS, THE INTERNAL WORKINGS AND SECURITY OF GOVERNMENTS AND THE STABILITY OF SOCIETY AS A WHOLE.
RANSOMWARE IS A BIG MONEY-MAKER FOR HACKERS WHEN THE INFECTED COMPUTERS ARE CRUCIAL TO THE OWNERS.
THE ATTACKS, SO FAR, HAVE DEMANDED OVER $1 BILLION FROM INFECTED USERS WORLDWIDE.
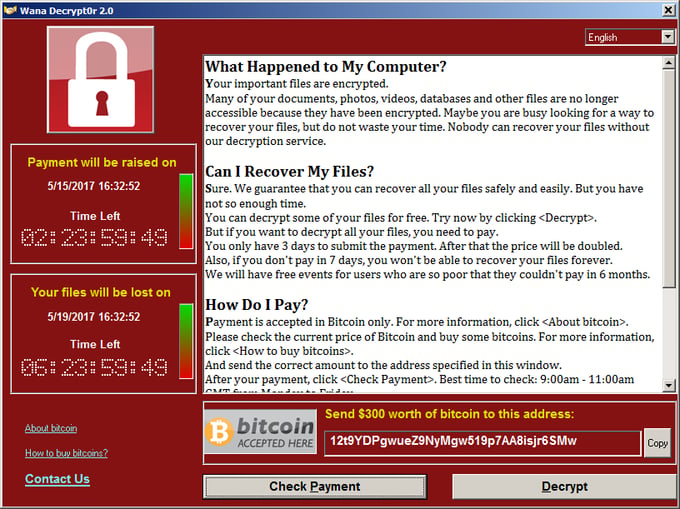
"Ransom demands start at $300 and increase after two hours to $400, $500 and then $600, said Kurt Baumgartner, a security researcher at Kaspersky Lab.
[IT SEEMS THAT, IN MOST CASES, PAYMENT IS DEMANDED IN BITCOIN, ACTUALLY. SEE THE BLOOMBERG ARTICLE <HERE> ]
Affected users can restore their files from backups, if they have them, or pay the ransom; otherwise they risk losing their data entirely."
THAT THIS RECENT ATTACK TARGETS HOSPITALS IS MOST DISTURBING.
IT SHOWS THE HACKERS' TOTAL DISREGARD FOR HUMAN LIFE.
"Patrick Ward, a 47-year-old sales director, said his heart operation, scheduled for Friday, was canceled at St. Bartholomew's Hospital in London.
Tom Griffiths, who was at the hospital for chemotherapy, said several cancer patients had to be sent home because their records or bloodwork couldn't be accessed."
"The malicious software has infected more than 75,000 computers in 99 countries worldwide on Friday, most of them concentrated in Russia, Ukraine and Taiwan, according to Dutch cybersecurity company Avast Software BV.
PLEASE, DO NOT OPEN EMAILS FROM SOURCES YOU AREN'T FAMILIAR WITH AND BE WARY OF EVEN EMAILS FROM TRUSTED SOURCES IF THEY HAVE ODD ATTACHMENTS.
DO NOT CLICK ON ATTACHMENTS ON SOCIAL MEDIA SITES OR INTERNET 'FORUMS'.
THOSE WITH OLDER WINDOWS OPERATING SYSTEMS WHICH WILL NOT BE UPDATED WITH 'PATCHES' TO PREVENT THIS, WINDOWS 7 THROUGH 8, ESPECIALLY, ARE COMPLETELY WITHOUT PROTECTION.
BIGGEST RANSOMWARE ATTACK IN HISTORY.
"It was believed to the biggest attack of its kind ever recorded.
The malicious software behind the onslaught appeared to exploit a vulnerability in Microsoft Windows that was supposedly identified [STOLEN FROM RUSSIA, ACTUALLY] by the National Security Agency for its own intelligence-gathering purposes and was later leaked to the internet.
Dozens of countries hit by huge cyberextortion attack
Associated Press May 12, 2017
NEW YORK (AP) — Dozens of countries were hit with a huge cyber-extortion attack Friday that locked up computers and held users’ files for ransom at a multitude of hospitals, companies and government agencies.
Britain’s national health service fell victim, its hospitals forced to close wards and emergency rooms and turn away patients.
RUSSIA HARDEST HIT
Russia appeared to be the hardest hit, according to security experts, with the country’s Interior Ministry confirming it was struck.
ACCORDING TO THE AVAST ANTIVIRUS BLOG...
We have observed a massive peak in WanaCrypt0r 2.0 (aka WCry) ransomware attacks today, with more than 57,000 detections, so far. According to our data, the ransomware is mainly being targeted to Russia, Ukraine and Taiwan.
[AS A RATHER PERSONAL BUT MAYBE IMPORTANT NOTE: I UNINSTALLED AVAST WHEN IT BEGAN TO BE AUTOMATICALLY CANCELLED AT 93% SCAN LEVEL AND NEVER FINISHED A FULL SCAN.
ONCE I HAD UNINSTALLED IT, WINDOWS 'TOLD' ME MY COMPUTER HAD NOT BEEN FULLY SCANNED FOR VIRUSES FOR 174 DAYS!
IT PAYS TO WATCH YOUR ANTIVIRUS SCANS RUN.
HOWEVER, I HAVE NOT YET FOUND AN ANTIVIRUS I AM HAPPY WITH.
FROM KASPERSKY TO AVG, ALL HAVE FAILED ME AT SOME POINT AND I HAVE LOST ENTIRE COMPUTERS TO VIRUSES.
ONE CAN GET REFUNDED THOSE COSTS, BUT IT TAKES TIME AND MUCH DOCUMENTATION BY AN I.T. 'COMPUTER EXPERT'/REPAIR SERVICE.
KASPERSKY WAS THE EASIEST TO DEAL WITH ONCE THEY HAD A LOOK AT WHAT WAS INFECTING MY FAVORITE COMPUTER YEARS BACK, FULL REFUND WITH SINCERE APOLOGY, BUT THAT COST ME 6 YEARS OF FILES AND DATA I CAN NEVER GET BACK, SO BE CAREFUL, FOLKS]
60 TO 70+ NATIONS ALREADY AFFECTED
All told, several cyber-security firms said they had identified the malicious software in upward of 60 countries, including the United States, though its effects in the U.S. did not appear to be widespread, at least in the initial hours.
SELF-REPLICATING RANSOMWARE, A COMPUTER CANCER
Computers were infected with what is known as ‘‘ransomware’’ — software that freezes up a machine and flashes a message demanding payment to release the user’s data.Mikko Hypponen, chief research officer at the Helsinki-based cyber-security company F-Secure, called it ‘‘the biggest ransomware outbreak in history.’’
Security experts said the attack appeared to be caused by a self-replicating piece of software that enters companies and organizations when employees click on email attachments, then spreads quickly internally from computer to computer when employees share documents and other files.
Chris Wysopal of the software security firm Veracode said criminal organizations were probably behind the attack, given how quickly the malware spread.
‘‘For so many organizations in the same day to be hit, this is unprecedented,’’ Wysopal said.
The security holes it exploits were disclosed several weeks ago by TheShadowBrokers, a mysterious group that has published what it says are hacking tools used by the NSA as part of its intelligence-gathering.
MICROSOFT'S 'PATCH', TOO LITTLE, TOO LATE...
Shortly after that disclosure, Microsoft announced that it had already issued software ‘‘patches’’ for those holes. But many companies and individuals haven’t installed the fixes yet or are using older versions of Windows that Microsoft no longer supports and didn’t fix.
By Kaspersky Lab’s count, the malware struck at least 74 countries.
In addition to Russia, the biggest targets appeared to be Ukraine and India, nations where it is common to find older, unpatched versions of Windows in use, according to the security firm.
Hospitals across Britain found themselves without access to their computers or phone systems. Many canceled all routine procedures and asked patients not to come to the hospital unless it was an emergency. Doctors’ practices and pharmacies reported similar problems.
British Prime Minister Theresa May said there was no evidence patient data had been compromised and added that the attack had not specifically targeted the National Health Service.
‘‘It’s an international attack and a number of countries and organizations have been affected,’’ she said.
SPAIN
Spain, meanwhile, took steps to protect critical infrastructure in response to the attack. Authorities said they were communicating with more than 100 energy, transportation, telecommunications and financial services providers about the attack.
Spain’s Telefonica, a global broadband and telecommunications company, was among the companies hit. The Spanish government said several companies had been targeted in the ransomware cyberattack.
Ransomware attacks are on the rise around the world.
Markus Jakobsson, chief scientist with security firm Agari, said that the attack was “scattershot” rather than targeted.
“It’s a very broad spread,” Jakobsson said, noting that the ransom demand is “relatively small”.
“This is not an attack that was meant for large institutions. It was meant for anyone who got it.”
On Twitter, whistleblower Edward Snowden blamed the NSA.
MANY HOSPITALS SEEMED TARGETED
U.S.
In 2016, Hollywood Presbyterian Medical Center in California said it had paid a $17,000 ransom to regain control of its computers from hackers.
BRITAIN
Krishna Chinthapalli, a doctor at Britain’s National Hospital for Neurology & Neurosurgery who wrote a paper on cybersecurity for the British Medical Journal, warned that British hospitals’ old operating systems and confidential patient information made them an ideal target for blackmailers.
He said many NHS hospitals in Britain use Windows XP software, introduced in 2001, and as government funding for the health service has been squeezed, ‘‘IT budgets are often one of the first ones to be reduced.’’
‘‘Looking at the trends, it was going to happen,’’ he said. ‘‘I did not expect an attack on this scale. That was a shock."
Ransomware attacks have been soaring.
The number of such attacks increased 50 percent in 2016, according to an April report from Verizon Communications Inc. These types of attacks account for 72 percent of all the malware incidents involving the health-care industry in 2016, according to Verizon.
“If @NSAGov had privately disclosed the flaw used to attack hospitals when they *found* it, not when they lost it, this may not have happened,” he said.
“It’s very easy for someone to say that, but the reality is the US government isn’t the only one that has a stockpile of exploits they are leveraging to protect the nation,” said Jay Kaplan, CEO of Synack, who formerly worked at the NSA.
“It’s this constant tug of war. Do you let intelligence agencies continue to take advantage of vulnerabilities to fight terrorists or do you give it to the vendors and fix them?”
HAS IT ONLY JUST BEGUN?
AS THE SOPHISTICATION OF THESE ATTACKS GROWS, WON'T ALL COMPUTERS BE AT THE MERCY OF THESE HACKERS, WORLD GOVERNMENTS AND THEIR CITIZENS?
I DON'T KNOW WHAT CAN BE DONE, I AM NO COMPUTER EXPERT BY ANY MEANS, BUT MAYBE OUR GOVERNMENTS SHOULD PRIORITIZE THIS TO THE TOP LEVEL.
WE INDIVIDUALS DON'T HAVE THE RESOURCES OR THE TECHNICAL MEANS TO PROTECT OURSELVES BEYOND TRUSTING ANTI-VIRUS SOFTWARE, ANTI-MALWARE, ETC, FROM COMPANIES WHICH HAVE FAILED US MISERABLY IN THE PAST.
SINCE ALL COMPUTERS AFFECTED WERE RUNNING AT LEAST SOME ANTI-VIRUS SOFTWARE, WHAT DOES THAT TELL US?
THEY'RE USELESS AGAINST SUCH ATTACKS.
________________
FURTHER READING, RELATED ARTICLES:
~How cyber attacks can crash economies, destroy governments and bring society to a standstill
~Are we headed for Cyber World War I?
~ For more on cybersecurity, check out the Decrypted podcast at the end of the Bloomberg article <HERE>.
~ WikiLeaks reveals CIA files describing hacking tools
~ Bray: If the CIA can compromise our gadgets, can’t others do the same?
~ NSA hacking tools were leaked online. Here’s what you need to know.
//WW
FACTS AND TRUTH, NO MATTER WHOM IT OFFENDS. POLITICALLY INCORRECT, 100% INDEPENDENT. THINK! IT'S NOT ILLEGAL ...YET!
No comments:
Post a Comment